 160
160
This Knowledge Base article will demonstrate steps one can take to identify attempts at spam or phishing from those outside our organization.
**These attempts can take place over text message or email; oftentimes, the party behind the attempt will impersonate a higher up member of our organization, usually someone public facing, so their name can be easily found and thus easily used**
**Should you encounter any email or text message you feel is suspicious, please alert IT by emailing [email protected] BEFORE taking any action requested therein; this includes clicking on links, or providing any information they've requested**
**In the case where erroneous behavior or ulterior motives may be at work, please hesitate to respond or take action requested, even if the email claims it is from a recently departed coworker**
Example 1:
- As noted by the red arrow, the sender's name (in this case, Lyon Steadman, Dr. Steadman's son) may seem legitimate, especially when they use a current member of our leadership team, such as our CEO or CFO; the email address, however, never matches up with the person they're pretending to be (in this case, a totally different name using Gmail, when we have thesteadmanclinic.com email)
- The body of such emails often contain a succinct request for a favor or task to be completed, sometimes asking for your cell phone #; in such instances, DO NOT provide your cell phone #.
- As noted by the green arrow, the email will often be signed using the same name as noted by the red arrow, along with title; this is done to give the email an air of authenticity.
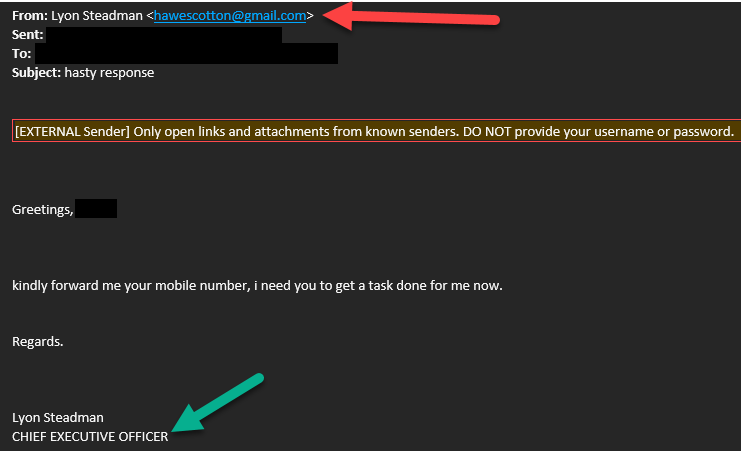
Again: Should you encounter any email you feel is even the least bit suspicious, please DO NOT click on any links contained therein, nor provide any info requested; rather, email [email protected] and we will assist you.
Example 2:
- As noted by the red arrow, the name appears official, but is really just jargon; the email address itself is a Gmail, which undermines the validity of the email immediately.
- The red box highlights a common occurrence within SPAM/Phishing communiques: bad grammar, misspelled words, or misuse of punctuation.
- The green box highlights the ultimate goal of this attempt: to get to someone high ranking, in the hopes they can be duped or misled in some way.
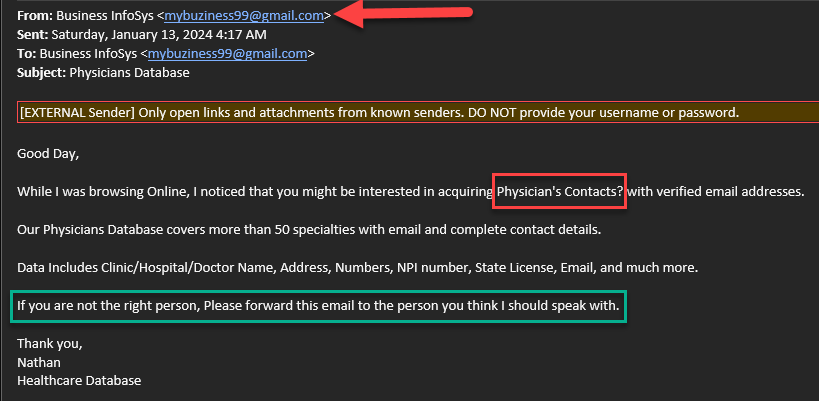
Again: Should you encounter any email you feel is even the least bit suspicious, please DO NOT click on any links contained therein, nor provide any info requested; rather, email [email protected] and we will assist you.
Example 3:
- When the attempts are made via text, the number is almost never part of our area code, as denoted by the red arrow; this is often clue #1 that something is amiss.
- The text typically contains clipped, incorrect language, and unusual punctuation, and the first message is usually signed, by a member of senior leadership, as if it were an email; this is noted by the green box, and can be seen as clue #2 of suspect origins.
- If a response to the first message is received, the sender usually replies stating they are busy but need a favor, often involving the purchase of gift cards; rest assured, no member of our leadership team would request such a favor through such means. Examples of this behavior can be found in the red boxes below.
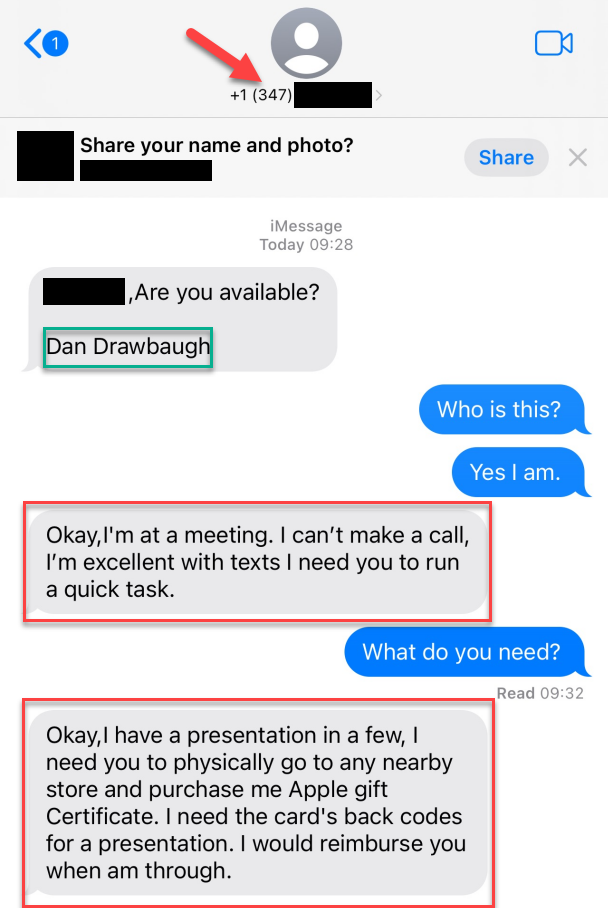
Again: Should you encounter any text you feel is even the least bit suspicious, please DO NOT click on any links contained therein, nor provide any info requested; rather, email [email protected] and we will assist you; no member of our leadership team will request via text that you spend your own money on gift cards for their purposes.



